Hello, dear readers!
I recently had the need to monitor user login activities on a Windows Server 2016 system. Ensuring only authorized access to critical servers is a fundamental part of cybersecurity. Traditional methods might involve sifting through the Event Viewer, a built-in utility to check various system logs, but this can be cumbersome. Therefore, I decided to write a PowerShell script that automates this process.
What Does the Script Do?
The PowerShell script fetches specific events—in this case, login events—from the Windows Security Event Log. It then extracts the username and the timestamp of each login event and displays it on the console. This could be particularly useful for auditing, monitoring unauthorized access, or even generating reports for analysis.
Prerequisites
To run this script, you'll need:
Windows Server 2016
PowerShell with administrative privileges
How to Run the Script
Open PowerShell as an administrator.
Copy and paste the script into the PowerShell console or save it as a
.ps1file and execute it.
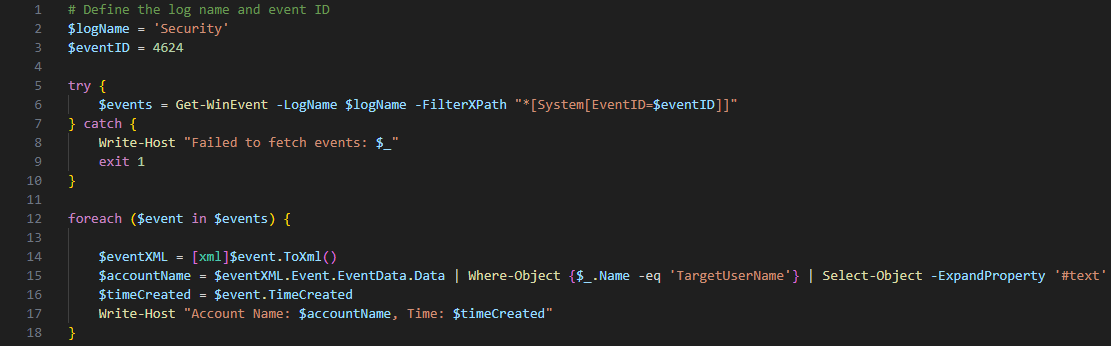
Here's the script:
Limitations and Considerations
You must run the script with administrative privileges to access the Security event log.
The script currently filters for Event ID 4624, which corresponds to successful login events. You can change this to any other Event ID based on your monitoring needs.
Conclusion
This script helped me save a lot of time by automating the login monitoring process. It's a simple yet effective way to keep an eye on your Windows Server 2016 systems. Feel free to modify the script to suit your needs, and I hope it helps you as much as it helped me!